Radio Interview: Staying Safe Online

We’ve heard a lot about online security in the news lately. From Russian hacking to email security, the subject has been a hot one in recent months, and for good reason. The internet is an integral part of our daily lives, and it is important that we take steps to ensure our private information remains so.
Recently, I spoke with Kendra Carr of Ludington’s WMOM 102.7 on the subject as part of her news segment. You can listen to the short interview, or read additional information on the topics discussed below.
Use Strong Passwords
With over 7 years under my belt handling client’s email accounts, server maintenance, and web accounts, one of the most common mistakes that I run across in regards to security is the use of weak passwords. Weak passwords are easily guessed, such as a name, birthday, or…maybe even the word ‘password’ itself.
A simple way hackers can gain access to an account is by using a brute-force attack. A brute-force attack typically utilizes software or a script that systematically enters 1 password at a time until the right one is entered. Using this form of attack, simple passwords can be discovered fairly quickly.
One of the easiest things you can do to help prevent unauthorized access to your accounts is to use a strong password. A good password should be long and include uppercase characters, lowercase characters, a combination of letters and numbers, and special characters (@, !, #, etc).
Protect Yourself on Wi-Fi Networks
Many people don’t realize that connecting to an unknown Wi-Fi network can be dangerous. It’s very easy for a hacker to setup a fake Wi-Fi hotspot, allowing them to collect information sent between your computer and your destination on the internet. This is called a man-in-the-middle attack.
The first step you can take to protect yourself in this situation, is to be smart about what you connect to. If the Wi-Fi network looks suspicious, it might be best not to connect to it.
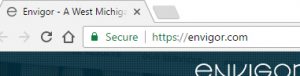
If you are connected to an open network, using websites that encrypt your data is a plus. Look for “https” in the website’s URL, or most browsers should display a little green lock (or something similar) before the URL if the website is encrypted (see below). Normal website connections pass information between your web browser and the web server in plain text, meaning that anyone in between can easily read that information. An encrypted connection on the other hand, will convert data into another form that only the intended parties can read. This means that your web browser and the web server can pass information back and forth securely, and the “man-in-the-middle” won’t be able to read your data.
Arguably, the best method you can use to protect yourself on an open network is to use a VPN (Virtual Private Network). A VPN essentially involves a piece of software on your computer that connects to a server owned by a trusted company (if you have the know-how, you can also create one that connects to your home-network). This connection encrypts all information between your computer and that trusted company.
There are many reputable VPN companies out there. We currently use a company called BolehVPN.
Use Two-Factor Authentication
Going back to the subject of passwords again, using something called two-factor authentication is a great way to protect your accounts in addition to having a strong password. Two-Factor authentication means providing two forms of identification to confirm that you are the rightful owner of your account: the first being your password, and the second, a code sent via text or generated by an app on your phone and only you have access to.
Many online services offer two-factor authentication. Facebook, Google, banking websites, etc. To see if a service that you use offers two factor authentication, Google search “how to setup two factor authentication for _______”.
Be Smart About Software
The last tip I can offer is to be smart about what software you download. Be sure it’s from a legitimate source and that you actually need it. Hackers can hide malware or malicious code in what might look like real software.
If you need help identifying legitimate software, get help from an IT professional like a technician at your local computer repair shop.
Thanks to Kendra and WMOM for inviting me to come in and discuss how to stay safe online.